En las últimas horas ha salido a la luz una nueva vulnerabilidad llamada Venom, que afecta a un buen número de plataformas de virtualización y que permitiría a un atacante escapar de un máquina virtual y acceder a otras en el mismo host. Afortunadamente se ha reaccionado rápidamente para mitigar los riesgos.

Virtualized Environment Neglected Operations Manipulation aka Venom (CVE-2015-3456) es una vulnerabilidad que afecta al software QEMU (todas sus versiones desde 2004), particularmente a su controlador de disco flexible (FDC). Esta vulnerabilidad permitiría como decíamos a un atacante con acceso a una máquina virtual y con privilegios para acceder al FDC conseguir acceso tanto al host como a otras máquinas virtuales corriendo en el mismo. Como vemos en el siguiente gráfico desarrollado por Crowdstrike.
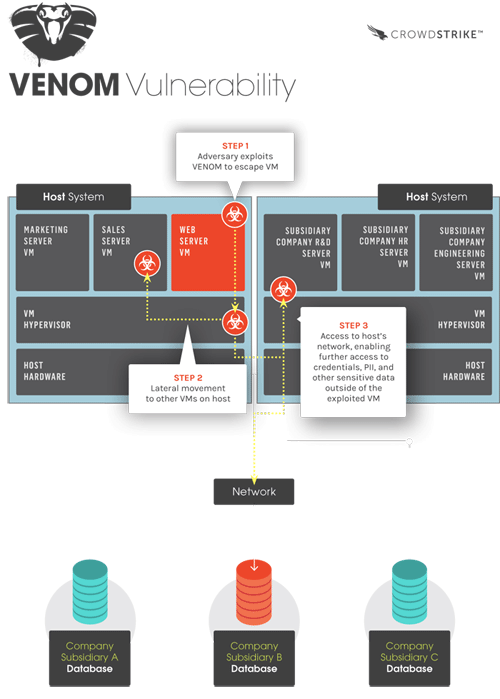
Este nivel de privilegios necesitaría de un usuario root en Linux y sería más sencillo en MV Windows, ya que practicamente cualquier usuario tendría acceso al mismo.
En un primer momento cundió el pánico ya que QEMU es utilizado en diferentes plataformas de virtualización como Xen, KVM, VirtualBox y el cliente QEMU que a su vez son usados por nombres tan importantes como Amazon, Oracle, Citrix o Rackspace. Afortunadamente estos proveedores se han movido rápidamente y ya han parcheado la vulnerabilidad. Otros sistemas como Hyper-V (Microsoft Azure) no se han visto afectados en ningún momento por este problema.
En caso que se necesite parchear cualquier otra máquina virtual, tanto Xen como QEMU han lanzado parches para solventar esta vulnerabilidad, por lo que se recomienda actualizar lo antes posible.
Tenéis mucha más información sobre Venom en la página que la propia Crowdstrike, empresa responsable del descubrimiento de esta vulnerabilidad, ha lanzado para ayudar a todos los afectados.
Fuente Crowdstrike
Now let’s know more about Venom:
Successful exploitation of Venom required:
Did venom poison Clouds Services?
"There is no risk to AWS customer data or instances," Amazon Web Services said in a statement.
Patch Now! Prevent yourself
Now let’s know more about Venom:
Successful exploitation of Venom required:
Did venom poison Clouds Services?
"There is no risk to AWS customer data or instances," Amazon Web Services said in a statement.
